Hi Guys,
During my recent bug bounty hunt, I came across a critical and yet simple vulnerability.It was payment price manipulation through which I could buy any product at the minimal cost. So, lets see what was the whole vulnerability-
I had to buy a wedding suit to attend a wedding ceremony so I went over internet where I came across a popular Indian shopping site and started my hunt. For some days, I was looking to find some bug in payment gateways and this came at the exact right time. So I captured the request before it hit the payment gateway —
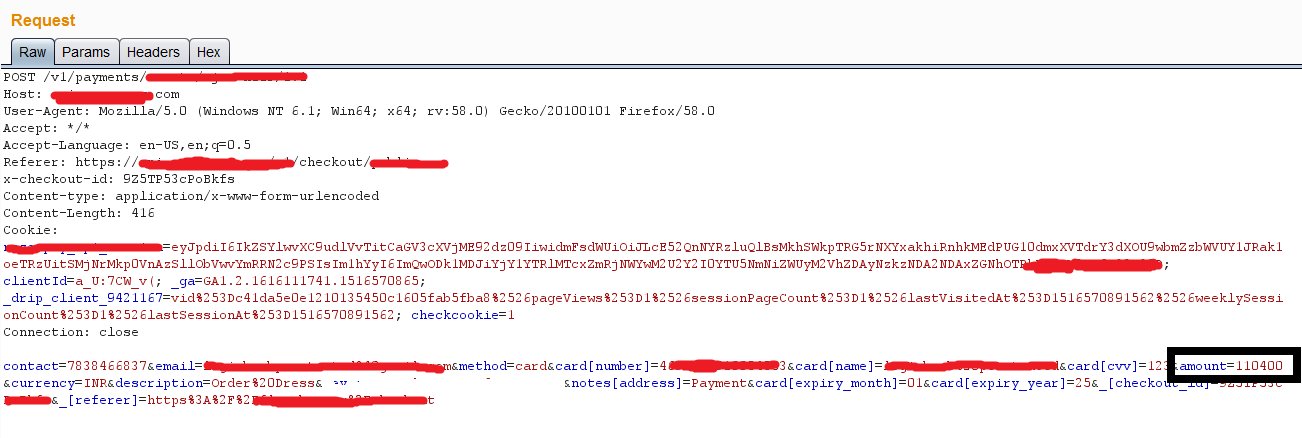
Note the amount parameter carrying the amount to be paid which is here as “Rs. 1104.00” (INR) and without any hesitation, I tampered the price value , entered “119” which means 1.19 (INR) and forwarded the HTTP request. Next, I was redirected to bank payment page as you can see below -
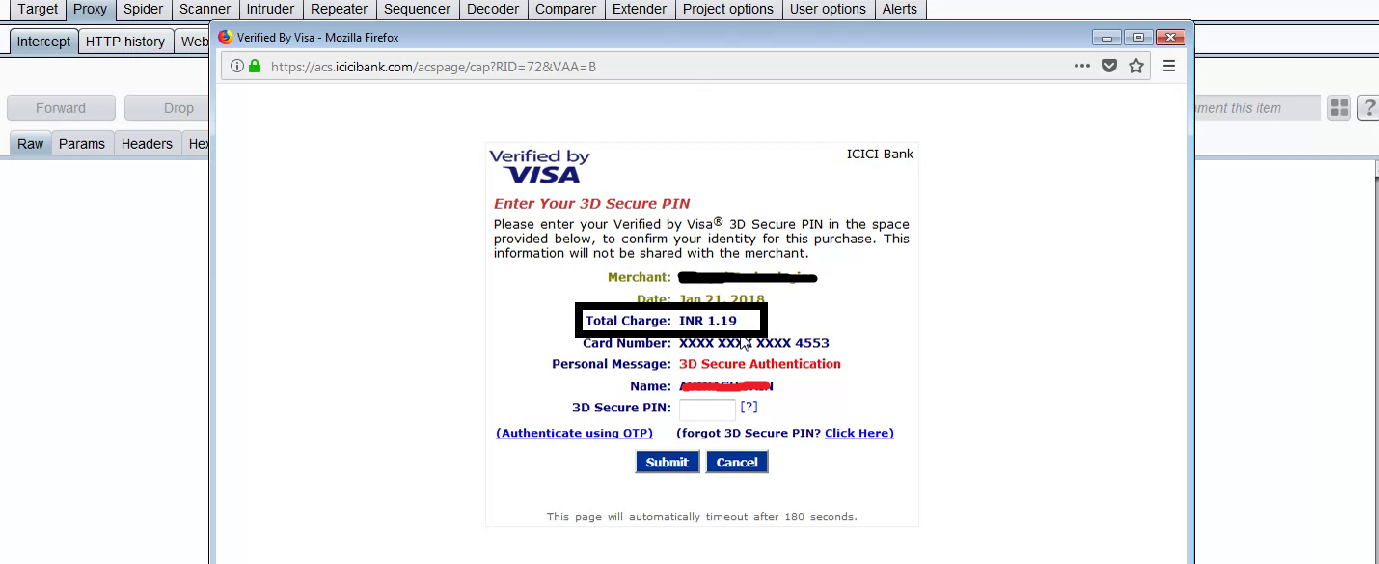
Whoaa! The final prize is “1.19” , I had a huge smile on my face and then I proceed further to get this —
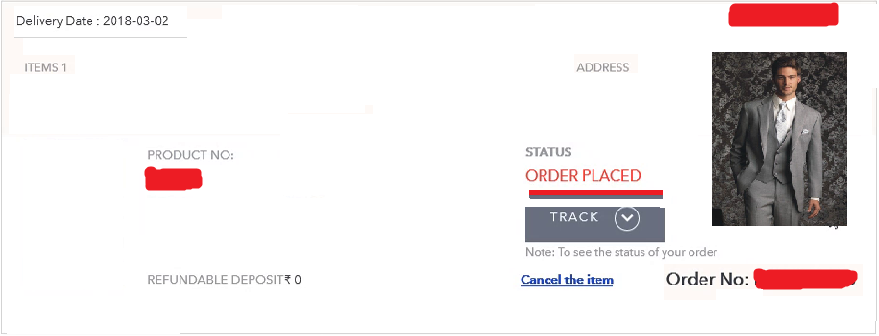
Order was placed successfully and I paid just 1.19 INR for 1104.00 INR :D. So simple yet so critical vulnerability and this happens when the prize is not validated back by the server. It was a surprise that still such simple loopholes exists and developers misses the validation of prize. Some secure steps that can be taken to prevent against such kind of attacks —
Always validate the prize back by the server.
Pull the prize from db and check whether it’s the same prize.
Refrain from sending amount in http request rather send only product id.
Thanks for reading!





0 Comments